Are you looking for a reliable way to manage your Raspberry Pi devices remotely while ensuring top-notch security? The RemoteIoT platform offers a free solution that allows you to manage SSH keys on your Raspberry Pi, providing secure and seamless remote access. With the increasing demand for remote device management, especially in IoT and embedded systems, having a secure method to access your Raspberry Pi is crucial. In this article, we will explore how to use the RemoteIoT platform to manage SSH keys on your Raspberry Pi, ensuring that your devices remain secure while being easily accessible from anywhere in the world.
Remote access to Raspberry Pi devices is essential for developers, system administrators, and IoT enthusiasts who need to manage their devices without being physically present. However, with the rise of cyber threats, it’s important to ensure that your remote access methods are secure. One of the most effective ways to secure your Raspberry Pi is by using SSH keys. SSH keys provide a more secure alternative to traditional password-based authentication, making it harder for unauthorized users to gain access to your device.
In this comprehensive guide, we will walk you through everything you need to know about managing SSH keys on your Raspberry Pi using the free RemoteIoT platform. From setting up your Raspberry Pi for remote access to generating and managing SSH keys, we’ll cover all the essential steps to ensure your device is both accessible and secure. Whether you’re a beginner or an experienced user, this guide will provide you with the knowledge and tools you need to manage your Raspberry Pi devices effectively.
Read also:Marcella Francesca Hetfield A Rising Star In The Entertainment Industry
Table of Contents
- Introduction to RemoteIoT Platform
- Why SSH Keys Are Important for Raspberry Pi
- Setting Up Your Raspberry Pi for Remote Access
- Generating SSH Keys on Raspberry Pi
- Managing SSH Keys with RemoteIoT Platform
- Securing Your Raspberry Pi with SSH Keys
- Common Issues and Troubleshooting
- Best Practices for Using SSH Keys
- Statistics and Data on Remote Access Security
- Conclusion
Introduction to RemoteIoT Platform
The RemoteIoT platform is a free and powerful tool designed to simplify remote device management, especially for IoT devices like the Raspberry Pi. It provides users with a secure and user-friendly interface to manage their devices from anywhere in the world. Whether you’re managing a single Raspberry Pi or an entire fleet of devices, RemoteIoT offers features that make remote access both convenient and secure.
One of the standout features of the RemoteIoT platform is its ability to manage SSH keys. SSH keys are an essential component of secure remote access, and RemoteIoT makes it easy to generate, store, and manage these keys. By using the platform, you can ensure that only authorized users have access to your Raspberry Pi, reducing the risk of unauthorized access and potential security breaches.
In addition to SSH key management, RemoteIoT offers other useful features such as device monitoring, automated updates, and real-time alerts. These features make it an ideal solution for anyone looking to manage their Raspberry Pi devices remotely while maintaining a high level of security. Whether you’re a hobbyist or a professional, RemoteIoT provides the tools you need to manage your devices effectively.
Why SSH Keys Are Important for Raspberry Pi
SSH keys play a crucial role in securing remote access to your Raspberry Pi. Unlike traditional password-based authentication, which can be vulnerable to brute-force attacks, SSH keys use cryptographic techniques to ensure that only authorized users can access your device. This makes SSH keys a more secure option for managing remote access to your Raspberry Pi.
When you use SSH keys, your Raspberry Pi generates a pair of cryptographic keys: a private key and a public key. The private key is stored securely on your local machine, while the public key is uploaded to your Raspberry Pi. When you attempt to connect to your Raspberry Pi via SSH, the server verifies the private key against the public key, ensuring that only authorized users can gain access.
Using SSH keys also eliminates the need to remember complex passwords, reducing the risk of human error. Additionally, SSH keys can be configured to require a passphrase, adding an extra layer of security. By using SSH keys, you can ensure that your Raspberry Pi remains secure while being easily accessible from anywhere in the world.
Read also:Sweetie Fox The Ultimate Guide To The Rising Star In The Digital World
Setting Up Your Raspberry Pi for Remote Access
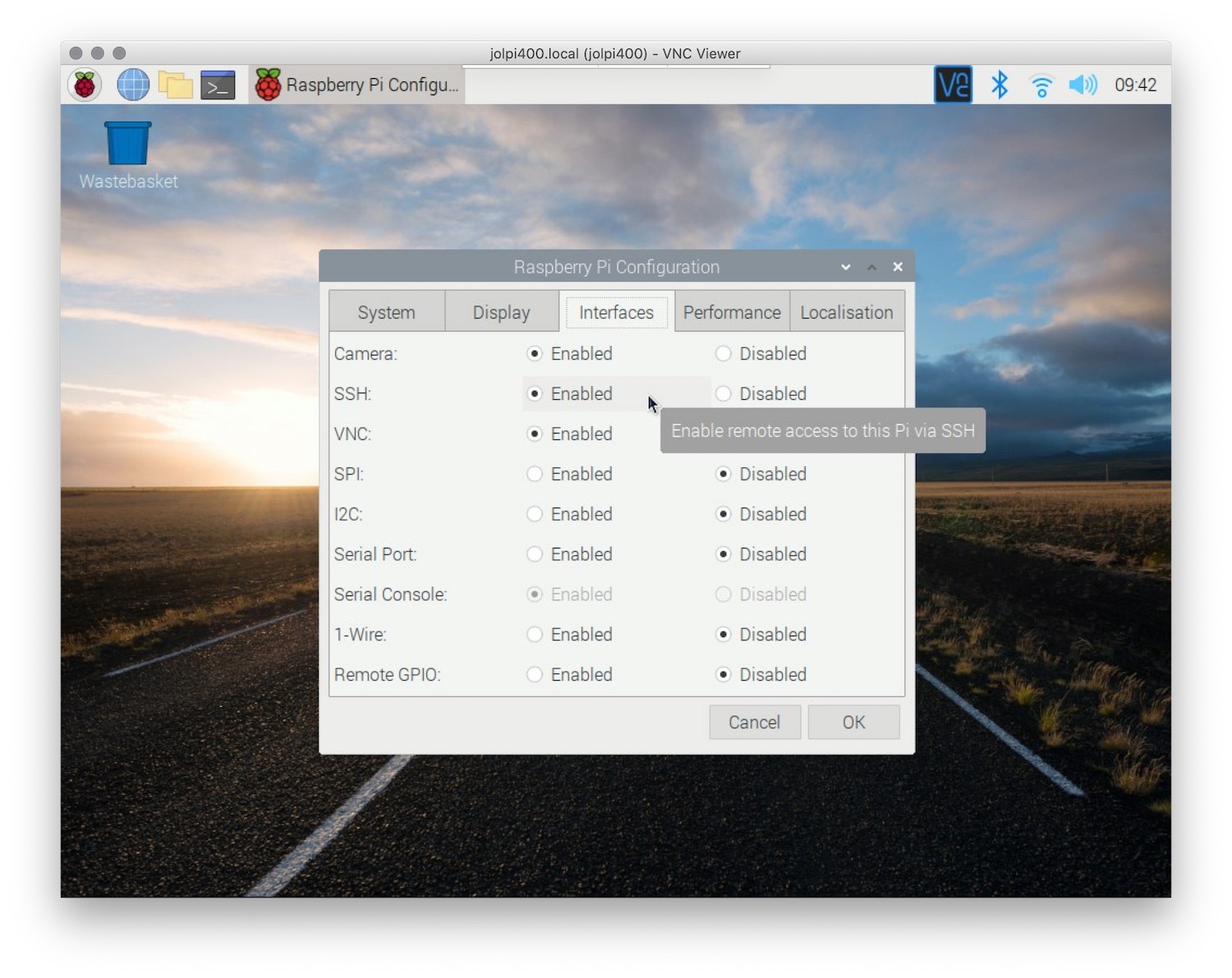
Before you can start managing SSH keys on your Raspberry Pi, you need to ensure that your device is properly set up for remote access. This involves enabling SSH on your Raspberry Pi and configuring your network settings to allow remote connections.
To enable SSH on your Raspberry Pi, follow these steps:
- Open the Raspberry Pi configuration tool by typing
sudo raspi-configin the terminal. - Navigate to the "Interfacing Options" menu and select "SSH."
- Choose "Yes" to enable SSH and exit the configuration tool.
Once SSH is enabled, you’ll need to configure your network settings to allow remote connections. This may involve setting up port forwarding on your router or using a dynamic DNS service to ensure that your Raspberry Pi is accessible from outside your local network.
Configuring Port Forwarding
Port forwarding is a technique used to allow external devices to connect to your Raspberry Pi over the internet. To set up port forwarding, follow these steps:
- Access your router’s configuration page by entering its IP address in a web browser.
- Navigate to the "Port Forwarding" section and create a new rule.
- Set the external and internal ports to 22 (the default SSH port) and enter your Raspberry Pi’s local IP address.
- Save the changes and restart your router if necessary.
Generating SSH Keys on Raspberry Pi
Generating SSH keys on your Raspberry Pi is a straightforward process that can be completed using the terminal. SSH keys provide a secure method of authentication, ensuring that only authorized users can access your device.
To generate SSH keys on your Raspberry Pi, follow these steps:
- Open the terminal on your Raspberry Pi.
- Type
ssh-keygen -t rsa -b 4096and press Enter. - You will be prompted to enter a file name for the key pair. Press Enter to accept the default location.
- Optionally, you can enter a passphrase to add an extra layer of security.
Once the keys are generated, you will find two files in the ~/.ssh/ directory: id_rsa (the private key) and id_rsa.pub (the public key). The private key should be kept secure on your local machine, while the public key can be uploaded to your Raspberry Pi.
Uploading the Public Key to Your Raspberry Pi
To upload the public key to your Raspberry Pi, use the following command:
ssh-copy-id pi@your_raspberry_pi_ip_address
This command will copy the public key to the ~/.ssh/authorized_keys file on your Raspberry Pi, allowing you to authenticate using the private key.
Managing SSH Keys with RemoteIoT Platform
The RemoteIoT platform provides a user-friendly interface for managing SSH keys on your Raspberry Pi. By using the platform, you can easily generate, store, and manage your SSH keys, ensuring that your device remains secure while being easily accessible.
To manage SSH keys with RemoteIoT, follow these steps:
- Log in to your RemoteIoT account and navigate to the "SSH Key Management" section.
- Click on "Generate New Key Pair" to create a new set of SSH keys.
- Download the private key and store it securely on your local machine.
- Upload the public key to your Raspberry Pi using the platform’s built-in tools.
By using RemoteIoT to manage your SSH keys, you can ensure that only authorized users have access to your Raspberry Pi, reducing the risk of unauthorized access and potential security breaches.
Securing Your Raspberry Pi with SSH Keys
Once you’ve generated and uploaded your SSH keys, it’s important to take additional steps to secure your Raspberry Pi. This includes disabling password-based authentication and configuring your firewall to restrict access to your device.
To disable password-based authentication, follow these steps:
- Open the SSH configuration file by typing
sudo nano /etc/ssh/sshd_configin the terminal. - Find the line that says
PasswordAuthentication yesand change it toPasswordAuthentication no. - Save the changes and restart the SSH service by typing
sudo systemctl restart ssh.
By disabling password-based authentication, you ensure that only users with the correct SSH key can access your Raspberry Pi, significantly reducing the risk of unauthorized access.
Common Issues and Troubleshooting
While managing SSH keys on your Raspberry Pi is generally straightforward, you may encounter some common issues. These include connection errors, key mismatches, and permission problems.
To troubleshoot these issues, follow these steps:
- Ensure that your Raspberry Pi’s IP address is correct and that your network settings are properly configured.
- Verify that the public key has been correctly uploaded to the
~/.ssh/authorized_keysfile on your Raspberry Pi. - Check the permissions of the
~/.ssh/directory and theauthorized_keysfile to ensure that they are set correctly.
If you continue to experience issues, consult the RemoteIoT platform’s support documentation or reach out to their customer support team for assistance.
Best Practices for Using SSH Keys
To ensure that your SSH keys remain secure, it’s important to follow best practices. These include using strong passphrases, regularly rotating your keys, and storing your private keys securely.
Here are some best practices for using SSH keys:
- Use a strong passphrase to protect your private key.
- Regularly rotate your SSH keys to minimize the risk of compromise.
- Store your private keys in a secure location, such as a password manager or hardware security module.
By following these best practices, you can ensure that your SSH keys remain secure and that your Raspberry Pi is protected from unauthorized access.
Statistics and Data on Remote Access Security
According to a report by Verizon, 80% of data breaches involve weak or stolen passwords. This highlights the importance of using secure authentication methods like SSH keys to protect your devices.
Additionally, a study by IBM found that the average cost of a data breach is $4.45 million. By using SSH keys and secure remote access solutions like RemoteIoT, you can significantly reduce the risk of a data breach and protect your Raspberry Pi devices from potential threats.
Conclusion
In conclusion, managing SSH keys on your Raspberry Pi using the free RemoteIoT platform is an effective way to ensure secure and seamless remote access. By following the steps outlined in this guide, you can generate, store, and manage your SSH keys, ensuring that your device remains secure while being easily accessible from anywhere in the world.
We encourage you to take advantage of the RemoteIoT platform’s features to manage your Raspberry Pi devices effectively. If you have any questions or need further assistance, feel free to leave a comment below or reach out to the RemoteIoT support team. Don’t forget to share this article with others who may find it useful and explore more content on our site for additional tips and guides.