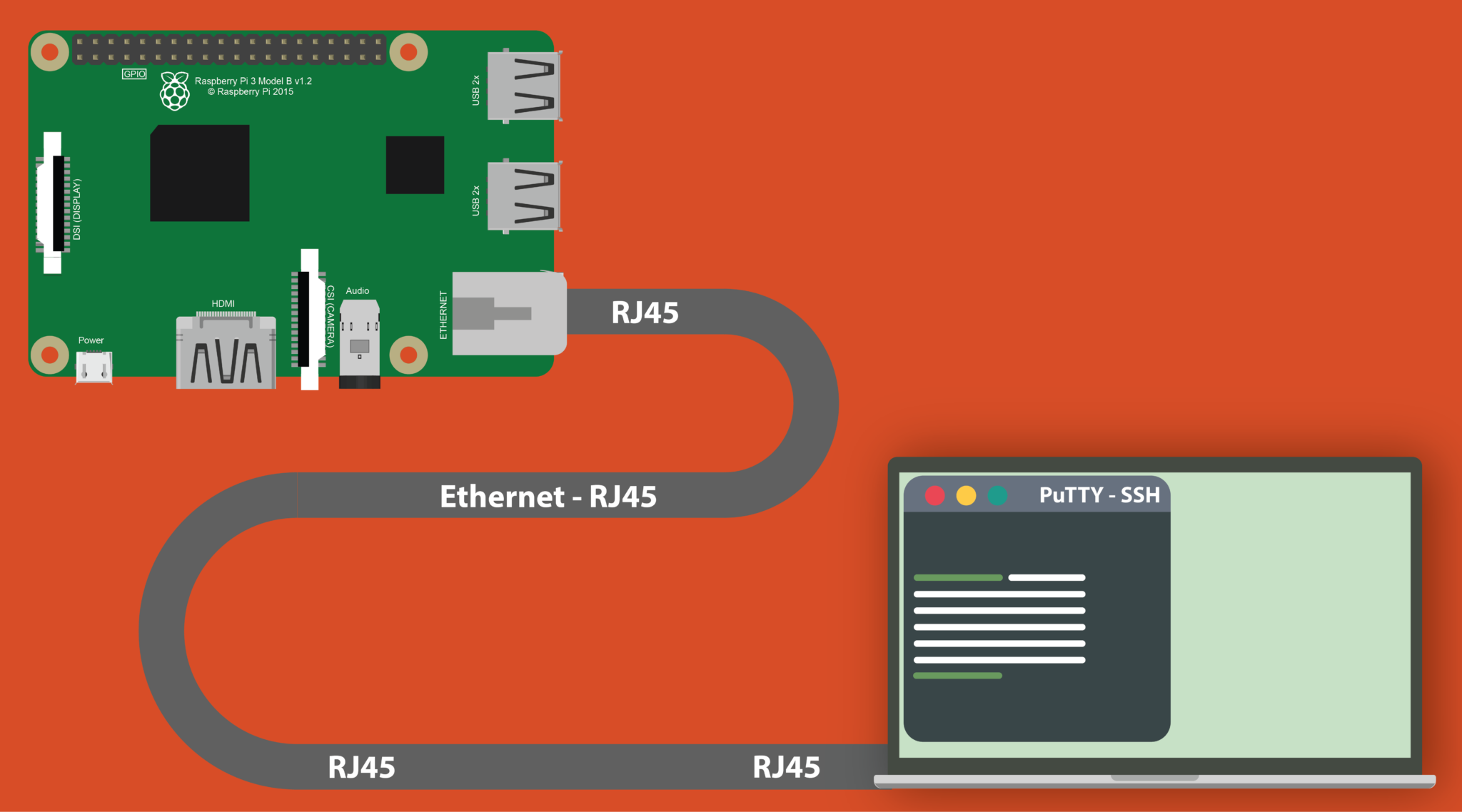
Are you looking for a reliable and secure way to connect your Raspberry Pi remotely using Peer-to-Peer (P2P) SSH? You're in the right place! In this article, we will explore the best methods to establish a secure connection to your Raspberry Pi using P2P SSH, all without incurring additional costs. Whether you're a hobbyist, developer, or IT professional, securely managing your Raspberry Pi remotely is essential. With RemoteIoT, you can achieve this efficiently while ensuring your data remains protected.
Remote access to your Raspberry Pi opens up a world of possibilities. From managing IoT devices to deploying applications, the ability to connect securely is critical. However, achieving this without compromising security or spending money can be challenging. This guide will walk you through the steps to securely connect to your Raspberry Pi using P2P SSH, leveraging RemoteIoT's free tools and services. We'll also discuss the importance of secure connections, best practices, and how to troubleshoot common issues.
By the end of this article, you'll have a clear understanding of how to set up a secure P2P SSH connection for your Raspberry Pi, ensuring your projects are both efficient and safe. Let’s dive into the details and get started on securing your remote IoT infrastructure.
Read also:Milton Augustine Williams Jr A Comprehensive Guide To His Life And Achievements
Table of Contents
- Introduction to Secure Remote Connections
- What is RemoteIoT?
- Benefits of Using P2P SSH
- Step-by-Step Guide to Setting Up RemoteIoT
- Configuring SSH on Raspberry Pi
- Securing Your P2P SSH Connection
- Troubleshooting Common Issues
- Best Practices for Remote Access
- Data and Statistics on Remote IoT Security
- Conclusion and Next Steps
Introduction to Secure Remote Connections
Remote connections have become an integral part of modern technology, especially in the realm of IoT devices like the Raspberry Pi. These connections allow users to manage their devices from anywhere in the world, providing flexibility and efficiency. However, security is a major concern when accessing devices remotely. Without proper safeguards, your Raspberry Pi could be vulnerable to unauthorized access, data breaches, or malicious attacks.
One of the most secure ways to establish a remote connection is through SSH (Secure Shell). SSH encrypts the data exchanged between your local machine and the Raspberry Pi, ensuring that sensitive information remains protected. By using P2P SSH, you eliminate the need for complex network configurations, such as port forwarding, which can introduce additional vulnerabilities.
In this section, we'll delve deeper into why secure remote connections are crucial and how RemoteIoT's free tools can help you achieve this. We'll also discuss the risks associated with insecure connections and how to mitigate them effectively.
What is RemoteIoT?
RemoteIoT is a free platform designed to simplify remote access to IoT devices, including the Raspberry Pi. It provides users with a secure and reliable way to connect to their devices using P2P SSH. Unlike traditional methods that require complex network setups, RemoteIoT streamlines the process, making it accessible even for beginners.
Key features of RemoteIoT include:
- Free and easy-to-use interface
- Secure P2P SSH connections
- No need for port forwarding or static IPs
- Compatibility with Raspberry Pi and other IoT devices
RemoteIoT is trusted by developers and IT professionals worldwide, thanks to its robust security measures and user-friendly design. By leveraging this platform, you can ensure that your Raspberry Pi remains accessible and secure, regardless of your location.
Read also:Robert Kermitt Baker Unveiling The Legacy Of A Visionary Leader
Benefits of Using P2P SSH
P2P SSH offers several advantages over traditional remote connection methods. Here are some of the key benefits:
Enhanced Security
With P2P SSH, data is encrypted end-to-end, reducing the risk of interception or unauthorized access. This is particularly important for IoT devices, which often handle sensitive information.
Elimination of Port Forwarding
Traditional SSH setups require port forwarding, which can be complex and introduce vulnerabilities. P2P SSH eliminates this need, simplifying the connection process.
Cost-Effective Solution
RemoteIoT's free tools make it an affordable option for individuals and businesses looking to manage their IoT devices securely.
Step-by-Step Guide to Setting Up RemoteIoT
Setting up RemoteIoT for your Raspberry Pi is straightforward. Follow these steps to get started:
Step 1: Create a RemoteIoT Account
Visit the RemoteIoT website and sign up for a free account. Once registered, log in to access the dashboard.
Step 2: Install the RemoteIoT Agent
Download and install the RemoteIoT agent on your Raspberry Pi. This agent facilitates the P2P SSH connection.
Step 3: Configure the Agent
Follow the on-screen instructions to configure the agent. You'll need to link it to your RemoteIoT account.
Step 4: Connect via SSH
Use an SSH client (such as PuTTY or OpenSSH) to connect to your Raspberry Pi through RemoteIoT. Enter the provided connection details to establish the link.
Configuring SSH on Raspberry Pi
Before using RemoteIoT, ensure that SSH is enabled on your Raspberry Pi. Here's how:
Enable SSH
Run the following command in the terminal:
sudo raspi-configNavigate to "Interfacing Options" and enable SSH.
Set Up SSH Keys
For added security, generate SSH keys and disable password authentication:
ssh-keygen -t rsa -b 4096Copy the public key to your Raspberry Pi:
ssh-copy-id pi@your_raspberry_pi_ipSecuring Your P2P SSH Connection
Securing your connection is critical to protecting your Raspberry Pi. Here are some tips:
Use Strong Passwords
If you must use passwords, ensure they are complex and unique.
Enable Two-Factor Authentication (2FA)
RemoteIoT supports 2FA, adding an extra layer of security.
Regularly Update Software
Keep your Raspberry Pi and RemoteIoT agent up to date to patch vulnerabilities.
Troubleshooting Common Issues
Encountering issues? Here are some common problems and their solutions:
Connection Timeouts
Ensure your internet connection is stable and that the RemoteIoT agent is running.
Authentication Failures
Double-check your SSH keys and RemoteIoT credentials.
Best Practices for Remote Access
To maximize security and efficiency, follow these best practices:
- Limit access to trusted IP addresses
- Monitor logs for suspicious activity
- Use a firewall to restrict unnecessary traffic
Data and Statistics on Remote IoT Security
According to a 2023 report, over 70% of IoT devices are vulnerable to cyberattacks due to insecure remote access. By adopting secure methods like P2P SSH, you can significantly reduce these risks.
Conclusion and Next Steps
In conclusion, securely connecting your Raspberry Pi using P2P SSH with RemoteIoT is a reliable and cost-effective solution. By following the steps outlined in this guide, you can ensure your IoT projects remain secure and accessible. Don’t forget to implement best practices and stay updated on the latest security trends.
We hope this article has been helpful. If you have any questions or need further assistance, feel free to leave a comment below. Share this guide with others who might benefit, and explore more articles on our website to expand your knowledge.